Ouroboros Functional Layering: Difference between revisions
No edit summary |
|||
| Line 22: | Line 22: | ||
** Flow control | ** Flow control | ||
Establishment of the flow, authentication and symmetric key distribution are implemented using a '''2-way handshake''' each. If the MTU allows, the authentication and symmetric key exchanges can be piggybacked in a single combined 2-way exchange, so within a 1 Round-Trip Time. See [[Flow Allocation]] for more details. | Establishment of the flow, authentication and symmetric key distribution are implemented using a '''2-way handshake''' each. If the MTU allows, the authentication and symmetric key exchanges can be piggybacked onto the flow establishment request/reply in a single combined 2-way exchange, so within a 1 Round-Trip Time. See [[Flow Allocation]] for more details. | ||
=== Network End-to-End layer / Flow Allocator === | === Network End-to-End layer / Flow Allocator === | ||
Revision as of 10:14, 13 October 2023
![]() This page is under construction
This page is under construction
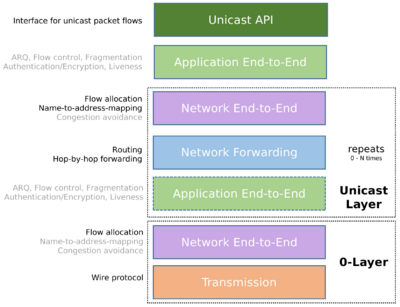
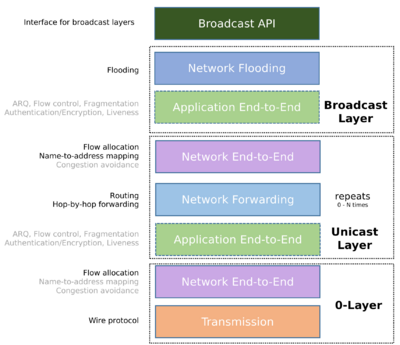
Unicast model
Unicast API
The Unicast API provides the interface for an application to create, manage and destroy unicast flows and read and write from and to these flows. The API is network-agnostic and provides application primitives for synchronous and asynchronous Inter-Process Communication. It supports message-based and (byte)stream-based communication.
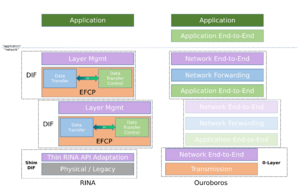
Application End-to-End layer
The application end-to-end layer provides the functionality to establish flows and make packet transmission on that flow reliable and secure. The application end-to-end layer can provide the following operations:
- Encryption (Public key or symmetric key)
- Authentication (validation/verification of certificate chains, HMAC)
- Integrity (hash-based checks such as CRC32)
- Reliability, implemented by the FRCP protocol
- Fragmentation
- In order delivery
- Discarding duplicate packets
- Automated-Repeat Request (retransmission of lost packets)
- Flow control
Establishment of the flow, authentication and symmetric key distribution are implemented using a 2-way handshake each. If the MTU allows, the authentication and symmetric key exchanges can be piggybacked onto the flow establishment request/reply in a single combined 2-way exchange, so within a 1 Round-Trip Time. See Flow Allocation for more details.